How to Evaluate Your File Transfer Protocol System
How to Evaluate Your File Transfer Protocol System
Contributed ContentFile Transfer Protocol can connect applications that have limited modes of integration. Still, FTP offers various security problems and can be extremely costly. You need to evaluate whether your business should update from FTP.
File Transfer Protocol (FTP) has become outdated for modern-day data exchange.
File Transfer Protocol is a system protocol used for exchanging files between a client and a server across a network.
FTP can be an effective method of connecting stove-piped applications, which work as standalone programs and offer limited modes of integration. However, FTP doesn’t scale to address new IT models and changing business needs. Relying on FTP can be a disadvantage for companies. Businesses need to overhaul FTP’s features and learn how to improve the system.
How Does an FTP Framework Work?
The Department of Defense developed File Transfer Protocol under its Advanced Research Projects Agency in 1969. The Department of Defense created FTP to move files across IP-based networks. This protocol allows users to send unencoded binary files over IP networks.
Binary files are files stored in binary format, which are computer readable and not human-readable. The picture below shows how the servers connect.
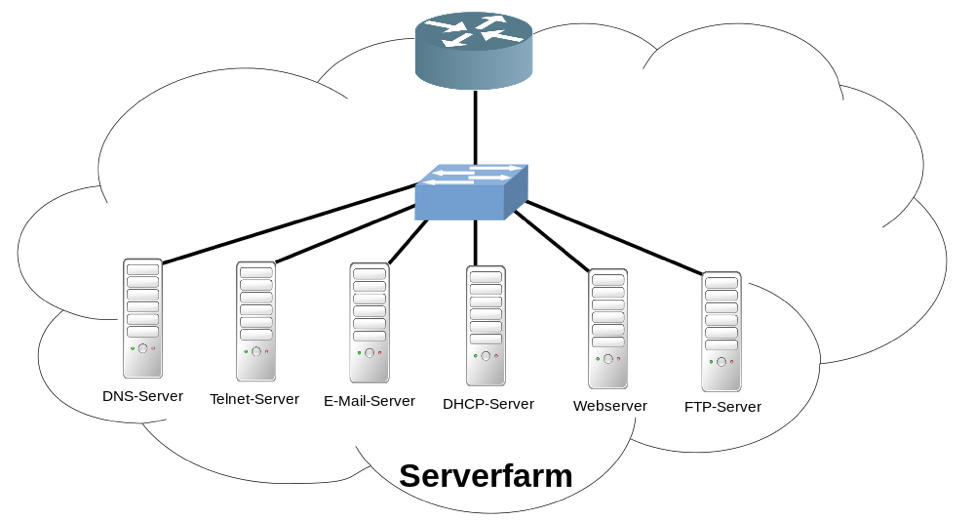
This illustration demonstrates how an FTP solution works. The FTP manager is installed in an ecosystem, which shares massive similarities with the windows explorer. Users need to configure the client software with the server address, username, and password.
The FTP client uses one connection, called port no. 21, for sending and receiving the data. This port functions like a "logical connection point" or “command port” and works with the Internet Protocol (IP) for sending commands.
The FTP server provides a list of all files back to the client for enabling an exchange of files. After this, the users can upload, download, and delete files.
The sender needs to publish binary data into packets which are received by target systems reassembled in order. These steps demonstrate how FTP allows people to send unencrypted, binary files through IP networks.
What Is the Client/ Server Model?
This protocol leverages the client/server model to move files. It enables users to configure files and also update network switches and routers. In a client/server model, the client opens a random port to initiate requests.
For instance, the FTP client opens port 1 to forward requests and uses port 21 to receive connection requests. Port 21 confirms the receipt of requests with an acknowledgment.
In this way, connectivity is established between the client and the server. Data transfer begins once this arrangement is established.
Using this system, an active FTP session is conducted via client and server.
Moving Away from FTP Systems
Businesses should be aware of the problems in the FTP system, which can slow productivity and hurt efficiency. Many FTP systems experience issues that cannot be resolved easily including:
Lack of Security
The client/server model is a non-secure way to transfer data. This model sends passwords, usernames, and other important information in clear text, which is unencrypted. Hackers can access this information, easily.
To encrypt files, FTP users need to upgrade to a more complex version like FTPS or SFTP.
Data transfer through FTP cannot be encrypted. Hosted FTP solution providers lack the features required for access controls, security, usability, and pricing options. This lack makes the FTP server vulnerable to spoofing attacks or brute-force attacks.
A brute-force attack occurs when a hacker tries all passwords until she or he can invade the database.
Similarly, a spoofing attack is when a malicious party pretends to be a legitimate user to breach networks, steal data, spread malware, and bypass access controls.
Due to this lack of security, sending sensitive data like payment data or health information through FTP is not advised.
The Absence of Drivers for Modern-Day Data Exchange
Core FTP systems need to be re-engineered to align with compliances like HIPPA.
FTP also does not track inconsistencies or monitor remote systems. Teams often struggle when they fail to track the source of the problem. FTP options lack access control options for sharing files with best practices.
Costly Overheads
Even a slimmed down FTP server with a basic hardware installation can cost at least $2500 to maintain. Additionally, there can be a license fee for using popular programs like Serv-U and GlobalScape.
These programs are leading information exchange solutions built for inbound and outbound file exchange.
Finally, set-up and bandwidth can be expensive.
FTP servers become cost centers as money goes into configuring windows (IP addresses, hostnames, provisioning), purchasing additional security licenses, creating user accounts, and developing directories or server permissions.
Enterprises squander a lot of money on hiring skilled architects for FTP projects.
Maintenance Issues
Teams face debilitating and recurring errors while backing up, monitoring, and governing FTP protocols. FTP connections are timed out when internet service providers block ports. Teams receive error messages when the system is connected with a proxy server.
A lot of time is wasted troubleshooting these problems.
It becomes difficult to support and update older FTP systems as the proprietary tooling gets too rigid to be scaled. The framework gains weight with each new change and unique customization.
Constant developer support and expertise are needed to support and update FTP systems. FTP maintenance quickly becomes a painful undertaking.
Alternatives to FTP
Archaic FTP systems tend to be difficult to operationalize. Sticking with FTP can be a true disadvantage for an enterprise. Here are some possible options to replace FTP solutions:
File Transfer Protocol Secure (FTPS)
FTPS is an upgraded version of FTP, which has security features, including Secure Sockets Layer (SSL). This feature enables digital certification, symmetric and asymmetric encryption, and message authentication code (MAC) algorithms for securing systems.
FTPS also runs on port 21 like FTP. This is a good option for enterprises that cannot completely replace FTP solutions.
Secure File Transfer Protocol (SFTP)
Although commonly mistaken as an FTP solution, SFTP operates on a single port called port 22. SFTP uses a secure channel between the source and target systems to prevent unauthorized disclosures during electronic data interchange (EDI).
Users need to be authenticated with user ID, password and Secure Shell (SSH) keys that encrypt the information stream. A single port advantage with these unique capabilities makes SFTP a great option.
Hyper Text Transfer Protocol Secure (HTTPS)
There are some major differences between HTTP and HTTPS protocols. Unlike HTTP, HTTPS can encrypt traffic with the help of Transport Layer Security (TLS). Layered security provides a secure channel for file transfer between partners.
TLS ensures that data cannot be changed without prior permission. HTTPS is the right solution for a use case where partners need a browser-based interface for data exchange.
Applicability Statement 2 (AS2)
AS2 protocol is a common transfer protocol for B2B transactions and runs on top of HTTPS. Therefore, the user also gets the Secure Sockets Layer (SSL) advantage available in FTPS platforms. SSL is a protocol that enables a secure channel between two machines operating in a network.
Apart from this, AS2 is equipped with a Message Disposition Notification (MDN) mechanism for an electronic return receipt. This mechanism helps users track EDI transactions like invoices, purchase orders, and ship manifests. MDN can be used for enforcing a non-repudiation clause in contracts.
In digital security, non-repudiation means an electronic signature that authenticates the origin and integrity of the data.
Managed File Transfer (MFT)
MFT is another secure option for making the electronic data interchange faster and efficient. It streamlines data between systems, employees, and partner networks. MFT bundles several options to streamline data exchange between enterprises and their partners. It helps enterprises adhere to compliances like PCI, DSS, HIPAA, and GLBA.
Users get advanced authentication and data encryption for secure and efficient file transfers. The below picture demonstrates how the files can transfer to different systems.
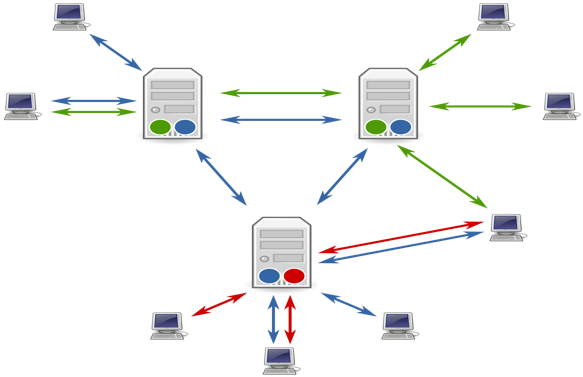
Remember that each protocol has distinct strengths and weaknesses. In complex B2B integration scenarios, it becomes difficult to predict which protocol will be required for a certain file transfer.
Organizations looking for bulk data transfer capabilities should consider a multi-protocol managed file transfer solution. Enterprises have the ability to adapt all these protocols at any given time for greater interoperability and performance.
Your Business Should Upgrade From FTP
There are many valid reasons for replacing the File Transfer Protocol (FTP). It is a standalone and outdated technology that is not fit for modern data exchange.
FTP protocol doesn’t secure data and doesn’t scale to cover the new-age data integration needs. Further, businesses can use a B2B integration system to manage customer data.
Replacing FTP with better alternatives can help an enterprise increase efficiency and productivity. Enterprises with FTP should evaluate how this protocol fits into their network and implement better standards to safeguard their business’s critical data.
