Cybersecurity Guidelines for Video Conferencing & Messaging Platforms

Cybersecurity Guidelines for Video Conferencing & Messaging Platforms
As remote work becomes increasingly common, video conferencing and messaging platforms have become essential tools for secure business communication. This article will discuss strategies for developing new secure video conferencing software or enhancing the cybersecurity of existing systems to safeguard your data from potential threats.
The rapid adoption of solutions to support remote workforces has exposed the vulnerabilities in video conferencing security that many companies rely on for communication.
While these tools are user-friendly, they often lack enterprise-grade security protocols, leaving businesses susceptible to significant protection and privacy risks. A respondent in an (ISC)2 survey noted that the COVID-19 pandemic provided the perfect conditions for a surge in cybercrime.
The widespread shift to remote work has led to IP-based audio and video conversations being targeted by sophisticated daily attacks. These attempts aim to either access valuable information or disrupt the system, rendering it unusable.
Read on to learn how to bolster the cybersecurity of your video conferencing and messaging systems to protect your valuable data from cyber threats.
Looking to firm up security? Connect with top cybersecurity providers on The Manifest.
Understanding Video Conferencing: An Overview
A device's camera and microphone capture video and audio input, which is then converted from analog to digital signals and transmitted over the internet. Codec software, responsible for compression and decompression, reduces the data size for faster transfer.
Upon reaching the recipient, the codec software decompresses the data and converts it back to analog signals displayed on a screen or played through speakers. Most video conferencing applications employ noise suppression and sound control software, necessitating high-speed internet connections and networks. Users can access these services either through an app or a browser.
Major players in the market, such as Microsoft, Zoom, WebEx, and Google, provide free video conferencing software. Numerous smaller and custom platforms can also be tailored to meet the specific needs of organizations and businesses. These platforms and apps can be integrated with many other tools, making them easy to use.
However, one persistent issue before and after the COVID-19 pandemic has been organizations' underestimation of video conferencing security. Consequently, users inadvertently expose their sensitive data to potential attackers who could gain unlimited access if successful.
Addressing Security Concerns in Video Conferencing
With the rise of remote work and quarantine measures, more people rely on video conferencing tools. Traditional security training around these tools has been limited and nonexistent for many new users. Even organizations with previously stringent security practices hastily adopted new platforms to maintain productivity, inadvertently creating a haven for hackers and cybercriminals.
Data transmission is often the weakest link in conferencing security during a video call, as it must traverse numerous public and private networks to reach its destination. If a hacker intercepts an unencrypted conference call, they could turn the stream into a surveillance tool, capturing and redistributing sensitive corporate information or classified intelligence.
Moreover, video conferences may be archived for future reference. Since both the media content and metadata (e.g., attendee lists, polls, shared materials) from these calls can contain sensitive information, data leakage poses a significant risk to video conferencing cybersecurity.
Vulnerabilities in Voice and Video Conferencing Platforms: Real-World Examples
Zoom, one of the most popular platforms, faced significant security issues during the early days of remote work in quarantine. "Zoombombing," where pranksters interrupted Zoom calls with inappropriate content, was a significant concern.
Zoom's default settings were largely to blame, as they didn't require meeting passwords and allowed participants to share screens. The platform also had to redesign its iOS app to remove code that sent device data to Facebook, enhancing its secure video conferencing features.
In March 2019, Cisco Webex Teams addressed two high-severity vulnerabilities in its video conferencing tools that could allow attackers to execute code on affected systems, compromising security policies. Earlier in the year, they fixed an issue that allowed unauthenticated users to join password-protected meetings.
Slack faced a critical vulnerability that led to automated account takeovers (ATOs) and data breaches, posing significant enterprise chat security risks. Its extensive integrations with AppStore apps also exposed potential vulnerabilities through malicious add-ons.
With its 25-character string meeting IDs and restrictions on external participants, Google Meet still lacks fully encrypted video conferencing.
Microsoft Teams, currently perceived as having better security, has also faced issues, such as a security flaw in early 2020 involving a 'malicious GIF' that could steal user data across a company. Some customers are still waiting for the platform to implement advanced security best practices from Skype for Business.
Twilio, a major US communications company, confirmed privacy issues with its video conferencing solutions after unauthorized access to customer account information. Twilio's two-factor authentication app Authy was also compromised, highlighting the importance of addressing video conferencing security risks.
Samsung experienced a data breach in September 2022, with an unauthorized third party accessing some US customer information. While Social Security and credit card numbers were unaffected, personal information such as names, contact details, and product registration information was compromised.
Signal, a popular voice and messaging app, confirmed a user data leak following a phishing attack on Twilio, the company providing phone number verification services for Signal. Affected users received messages urging them to re-register. Still, Signal maintains that the attacker no longer has access to sensitive data and that Twilio has shut down the attack.
Enhancing Cybersecurity in Video Conferencing: Essential Tips
Security is critical to video conferencing, but how can you avoid common mistakes and ensure robust protection? Here are critical tips for securing your video conferences:
- Require Passwords and Multi-factor Authentication: Request a password for meeting access and utilize multi-factor authentication to verify authorized participants.
- Regularly Update Software: Apply security patches to ensure up-to-date software protection, and download official releases to avoid malware.
- Review Privacy Policies: Understand the tool's privacy policy and data storage practices. Opt for vendors that don't store meeting recordings on their servers and designate a responsible party for data storage within your organization.
- Monitor Attendee Access: Track meeting participants and use notification systems to alert you when someone new joins.
- Implement Waiting Rooms: Allow the host to control access to meetings by utilizing waiting room features, enabling them to screen incoming participants.
- Encrypt Meeting Recordings: Use end-to-end encryption and password protection to secure sensitive data from third-party access.
- Foster a Secure Conferencing Culture: Encourage employees to adopt best practices in video conferencing, ensuring that tools alone don't determine your security.
- Verify Unknown Phone Numbers: Confirm the identity of participants dialing in from unknown numbers and remove uncooperative individuals. Ensure your application requires dial-in passwords and avoid sharing full meeting links publicly.
- Set Notifications for Meeting Forwarding: Enable alerts for forwarded meeting invites and verify any additional participants.
- Restrict File Sharing in Chat: Limit file sharing within conference chats to prevent unauthorized access to private documents or the spread of malware.
- Opt for Business or Enterprise Plans: Invest in enterprise licenses that offer greater control and access to additional privacy features to meet your organization's needs.
Tailored Solutions for Comprehensive Cybersecurity
While the previously mentioned measures can reduce cybersecurity risks during video conferences, they only partially eliminate the problem. Developing a custom video conferencing tool with bespoke security protocols to protect all communications and shared data can be a more effective solution.
Integrating Security into the Software Development Life Cycle (SDLC)
Incorporating security throughout the entire SDLC enables the delivery of high-quality, highly secure products to the market. SDLC is a framework for creating an application from inception to decommissioning.
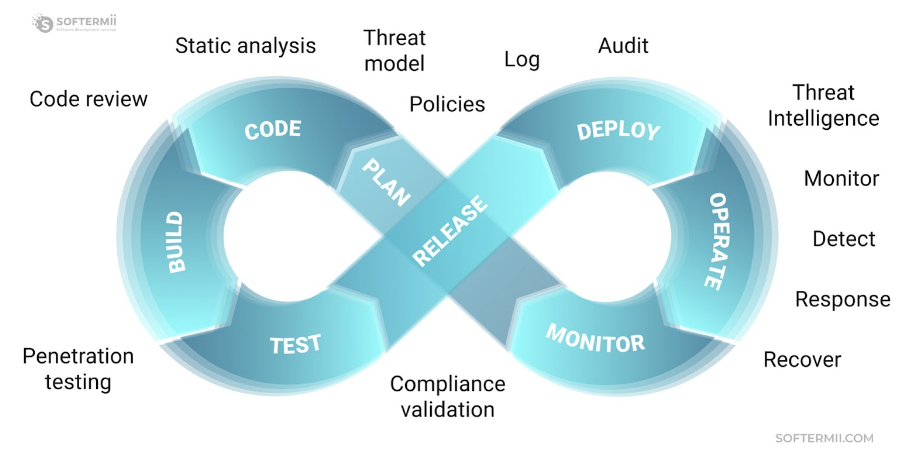
Traditionally, companies conducted security-related activities during the testing stage, near the end of the SDLC. However, integrating security testing across the SDLC helps discover and address vulnerabilities earlier, effectively building security from the ground up.
Security assurance activities include architecture analysis during design, code review during coding and build, and penetration testing before release.
Implementing DDoS Attack Protection Services
Securing software and data from cyber threats can involve DDoS attack protection services. A Denial of Service (DoS) attack is a malicious attempt to disrupt the availability of a targeted system, such as a website or application, for legitimate users.
Attackers typically generate large packets or requests, eventually overwhelming the target system. Multiple compromised or controlled sources are used in a Distributed Denial of Service (DDoS) attack.
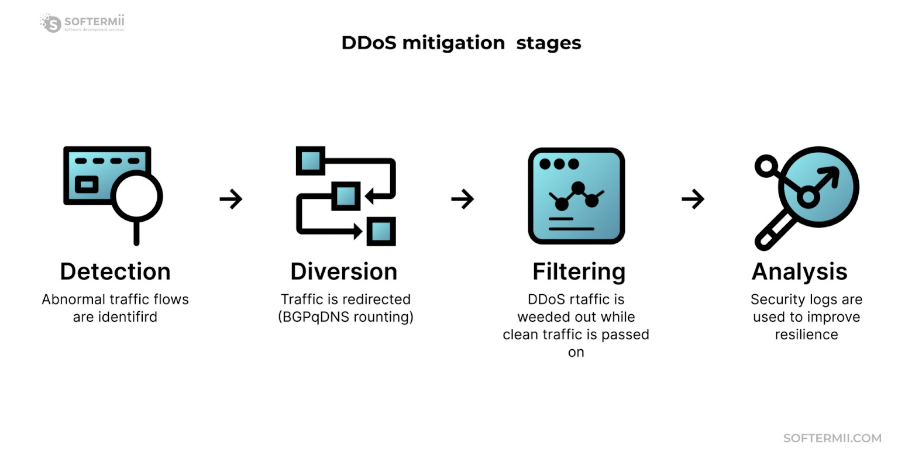
Mitigating DDoS attacks may involve minimizing the surface area, limiting attack options, and centralizing protections. It can be achieved by placing computation resources behind Content Distribution Networks (CDNs) or Load Balancers and restricting direct Internet traffic to specific infrastructure components like database servers. Firewalls or Access Control Lists (ACLs) can also control the traffic reaching the application.
Secure Media Transmission
Real-time Transport Protocol (RTP) is the dominant protocol for transmitting voice and video over IP networks. It is an application-level protocol, with its core defined in RFC3550.
Throughout RTP's lifetime, various attempts have been made to enhance its security, leading to the development of Secure Real-time Transport Protocol (SRTP) variants such as ZRTP, SDES, MIKEY, and DTLS-SRTP. The key difference between these variants is their methods of exchanging keys for securing conversations. We'll focus on DTLS-SRTP, which is the foundation of WebRTC for voice and video transmission. WebRTC mandates that all communications be secured using DTLS-SRTP, with specific requirements.
DTLS-SRTP has demonstrated its capacity to provide strong encryption for media payloads carried over RTP protocol when all other security criteria are met. SRTP doesn't encrypt packets entirely, only the actual media payload portion. RTP headers remain unencrypted and can be viewed if captured, but they don't contain sensitive information.
End-to-end encryption
Discussing video conferencing security necessitates addressing end-to-end (e2e) encryption. WebRTC media server is renowned for its default e2e encryption capabilities, utilizing three primary topologies in video conferencing:
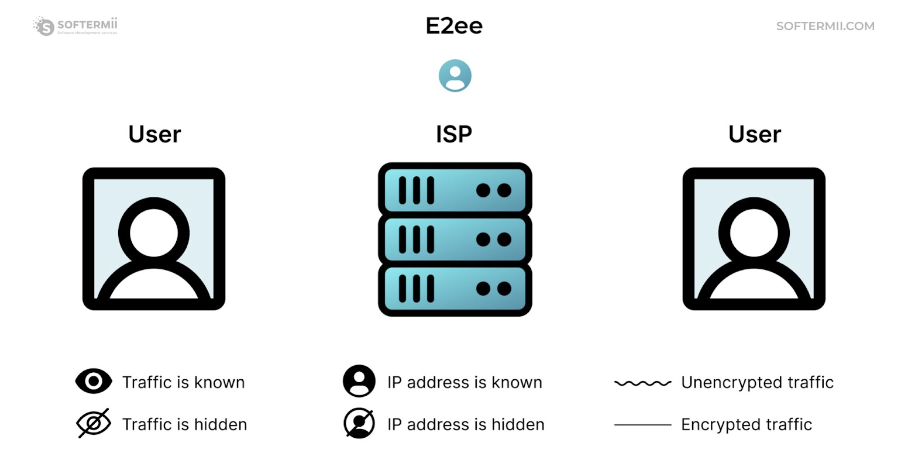
End-to-end encryption ensures that data transmitted between participants is encrypted at the source and only decrypted at the destination, preventing unauthorized access to sensitive information. This is critical for maintaining privacy and safeguarding the integrity of video conferences, especially in an age where cyber threats are increasingly prevalent.
Mesh
In this topology, each participant establishes connections with all other participants. The advantages include true e2e security and no intermediate servers intercepting traffic.
However, the drawbacks are limited scalability due to separate encoding and sending of audio/video streams by each participant, consuming significant CPU and bandwidth. It also lacks a robust recording mechanism, integrations, or optimizations.
MCU (Multipoint Control Unit)
Participants connect to a central server and send their audio and video streams. The server receives streams from all participants, mixes them, and sends a single audio and video composite stream to each participant.
The advantage is the significant reduction in client-side bandwidth and complexity. However, the server requires extensive CPU resources to decode and encode frames for every participant.
SFU (Selective Forwarding Unit)
SFU topology is a compromise between MCU and Mesh. Participants negotiate a connection with the central server and send their audio and video streams.
The server receives packets from a participant and sends copies to all other participants without decoding the payload. This topology is commonly used in modern video conferencing platforms (e.g., Google Meet, Zoom, MS Teams) and can be combined with an additional MCU server for recording or streaming purposes.
Secure Signaling
While WebRTC mandates media security in detail, it is signaling agnostic, without an RFC standard or API implementation. Secure WebSocket connections are recommended for transport layer security from a browser perspective. Still, WebRTC signaling can also be organized over HTTPS requests.
When using HTTP, it's crucial to address security considerations. For connecting servers to third-party systems like SIP trunks, opt for vendors that support SIP over TLS and SRTP in any form to achieve PSTN connectivity. Choose reliable, battle-tested solutions, such as Kamailio or OpenSIPs for Session Border Controllers, offering SIP traffic sanitizing, topology hiding, traffic throttling, and spam detection.
It is important to note that key exchange, encryption algorithms, and overall topology should be chosen case by case.
Enhancing Video Conferencing Security: A Must for Businesses and Legal Compliance
Securing video conferencing is crucial for a company's well-being and is also mandated by law. Regulations such as the Health Insurance Portability and Accountability Act (HIPAA), the Sarbanes-Oxley Act of 2002, and GDPR rules require medical providers, financial institutions, and other businesses to protect all digital data associated with their customers and patients, including electronic transmissions of personal client data during video conferences.
Nonetheless, a recent study conducted by data security firm Rapid7 revealed a pressing need for enhanced vulnerability management practices. Companies of all sizes, from small and mid-sized businesses to large corporations, must ensure secure communication in virtual environments. Custom software development is the most effective way to address video conferencing security concerns.
Find the right cybersecurity company on The Manfiest.
