7 Steps You Should Take to Improve Mobile App Security

7 Steps You Should Take to Improve Mobile App Security
Learn what steps you can take to ensure you build a secure mobile app. Read this article before you start coding.
In a world where data breaches and cybersecurity threats are frequent, it becomes a top priority to ensure your app’s security.
Let’s see what kind of security issues a mobile app can face and how app makers and developers can address them adequately.
We'll examine:
- What are some common mobile app security issues?
- Unintended data leakage
- Poor authorization/authentication
- Improper session handling
- Broken cryptography
- What are some steps to address these issues?
- Hire a security team
- Be careful with APIs
- Use tokens to handle sessions
- Use high-level authentication
- Use the best encryption tools and techniques
- Impose access policies
- Test, test, and test again
Common Mobile App Security Issues
Unfortunately, there are many security issues that an app might face.
Unintended Data Leakage
Unintended data leakage refers to the storage of essential app data in insecure locations on the mobile device. This happens when the data is stored in a location on the device that is available for other apps.
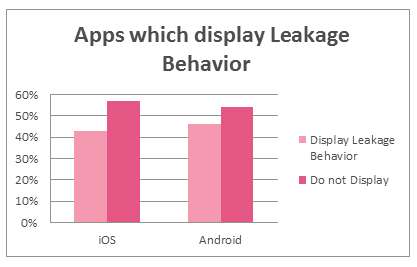
The ultimate result can be a breach of user privacy which can lead to unauthorized data usage. Unintended data leakage can have a few causes, such as bugs in the operating system or negligence of security by the developers.
Poor Authorization/Authentication
Unlike with web apps, mobile app users are not always connected to the internet.
When apps are offline, they are usually unable to distinguish between users. Therefore, mobile apps might require offline authentication, creating a unique security problem.
If the offline authentication is weak or is missing entirely, hackers can operate the mobile app anonymously, leading to data protection issues. In such a scenario, the users with low permissions can operate the app the same way as the administrators can.
Improper Session Handling
Improper session handling happens when the previous session continues, even when the user has switched away from the app.
Many e-commerce apps allow long sessions; app makers do this to speed up the buying process. But this practice can pose security risks, especially if the smartphone is stolen. Anyone who accesses the device can take or manipulate essential user data.
Broken Cryptography
Despite its usually secure nature, encryption can fail.
Encryption works by securing data with “keys” that must be present to access the data. Only certain users are able to hold the keys.
Hackers can benefit from users who may store their encryption keys in insecure locations.
What Steps Can Be Taken to Address App Security Issues?
The good news is that app makers can take a few steps to address app security issues. See them below:
Step 1: Hire a Security Team
If you care about your app's security, it’s an excellent idea to incorporate the security team from day one.
Make sure to allocate enough resources to security. Start planning the security measures you will be taking with a dedicated team.
Also, every time there is a change to make on the app or a significant revision to plan, make sure to consult the security team, so they know what to do if something unexpected happens.
Step 2: Be Careful with APIs
An application programming interface, or API, is a crucial part of backend development, allowing applications to talk to each other. But since they are outward-facing, they can be a security headache.
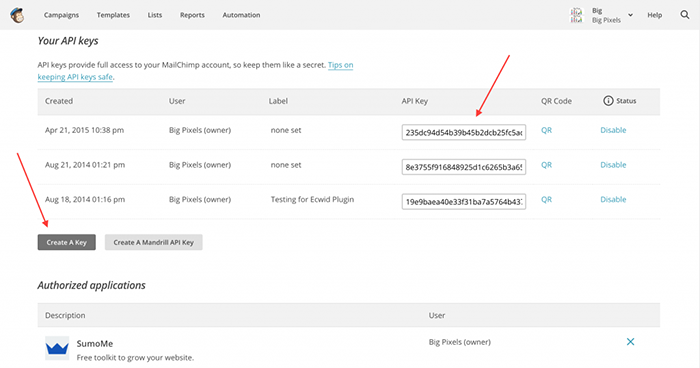
As you can see above, each application must receive a “permission key” (API key) before they can interact or make changes on the platform you’re working on.
Taking it even further, you could incorporate an API gateway to further tighten mobile app security.
Step 3: Use Tokens to Handle Sessions
A token is a “small hardware device carried by a user to authorize access to a network service.”
In the modern app world, developers use tokens to manage user sessions more productively. You can easily revoke a token.
Step 4: Use High-Level Authentication
As mentioned above, many security breaches happen due to weak authentication. Hence, it is becoming more critical to use stronger authentication.
Authentication often refers to passwords. It’s your job as an app maker to encourage your users to be careful with passwords.
For example, you can design your app so that it only accepts strong alphanumeric passwords that can be renewed every six months.
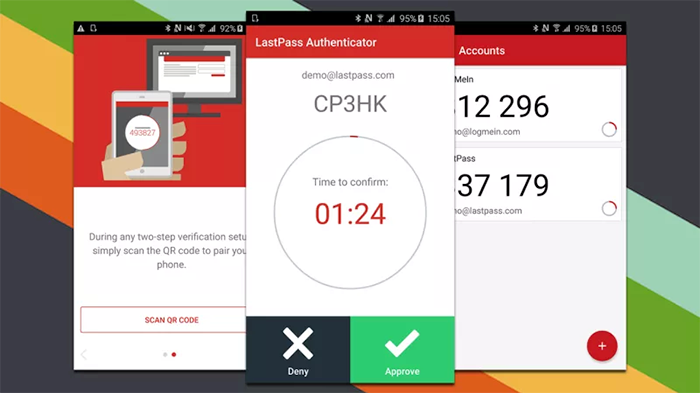
Dual-factor authentication is also a great way to secure a mobile app. If your app allows dual-factor authentication, then the user will be required to input a code sent to his or her texts or email upon logging in.
More modern authentication methods include biometrics such as a retina scan and fingerprints.
Step 5: Use the Best Encryption Tools and Techniques
The number one thing to do for better encryption is to decide on key management. Store the keys in secure containers. Never store them locally on the device.
Step 6: Impose Access Policies
In order to reduce your app’s attack surface, make sure to use only secure libraries and frameworks. The app you are building should align with corporate policies applied by the organization’s IT administrators or by Google Play and Apple's App Store.
Step 7: Test, Test, and Test Again
Let’s face it - a lot of developers don’t test their code. QA is a crucial part of building quality code. That’s why the application security part of the QA process is key to creating an outstanding mobile app.
In order to have a secure app, your QA team should review the code regularly and identify security loopholes that might result in data breaches.
Secure Your Mobile App
App makers must comprehend the risks posed by cybersecurity threats and data breaches while building their mobile apps. By implementing the above-mentioned mobile app security measures, they will be able to safeguard both the apps and the data within.
These measures are not difficult to implement. App makers and developers need to take a comprehensive approach toward developing apps and should consider all the factors that affect app security.
